I was doing a CTF which required me to find the usernames of users of a wordpress website for a brute force attack, even though there is an option to brute force both the username and the password it can be a huge waste of time.
Also there are instances which website admin takes extra precautions to change the default “wp-admin” directory to prevent users from finding the admin logging page which can be bypassed finding out the authors name of the website.
Method 1: Using the Json REST API of wordpress
Use the following URL with your site name in it
https://www.example.com/wp-json/wp/v2/users/1
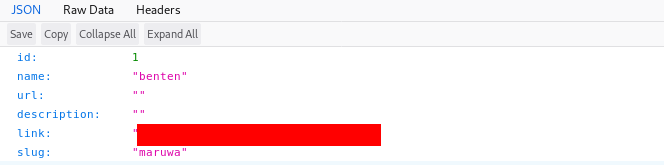
Response of the website after the request
This is caused because Wordpress exposes some REST APIs by default, allowing anyone to use them.
Method 2: Using the query parameter /?author=1
Append the website address with the following parameter to the end, and the author number should be incremented if there are more than one author
https://www.example.com/ /?author=1
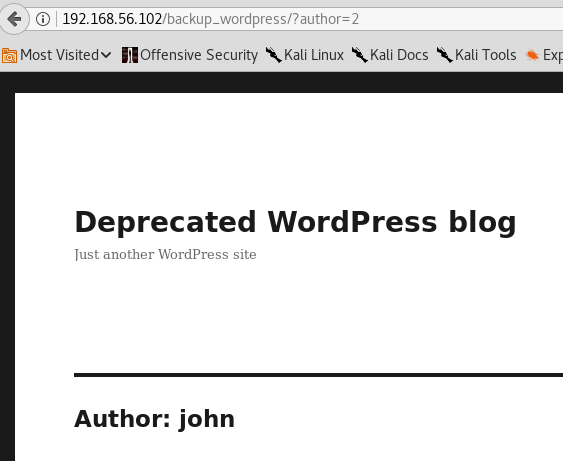
Response for the query parameter
Automation is everything
I whipped up a python script for these tests and there will be more improvements to it soon like plugging detection and Wordpress version detection.
You can get it from here
