There is a story about how I learned about this feature(yes it is a feature) in Linux systems.
in my university first year most computer science students started using some kind of a Linux OS. And everyone was talking about how cool and secure it is and one of my fellow students did a strange challenge that he can gain access to anyone’s Linux system. Crazy right? that is what I thought too until he proved it to us that it is a pretty easy thing to do.
First I will demonstrate how it is done in your favorite Kali Linux OS then we can talk about why it exists, finally the fun stuff, lets dive into some basics about kernel and system boot process. Remember as everything here, these posts are for the educational purpose only.
- First we need to get into the GRUB menu, if it does not show up use the “ESC” to get into the menu
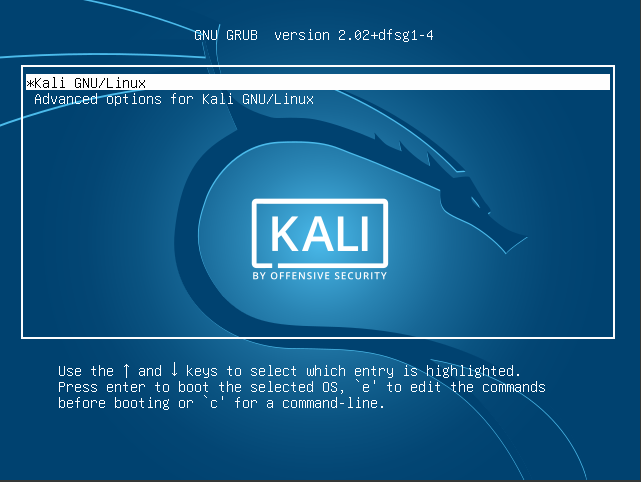
2. Now press “e” to edit the GRUB and you will enter a screen with GRUB commands.
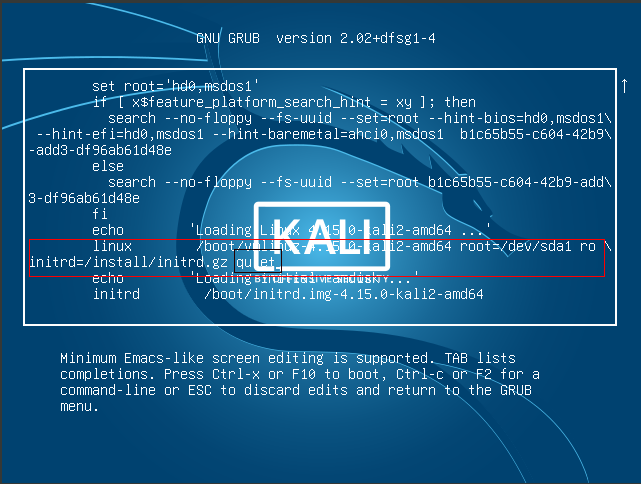
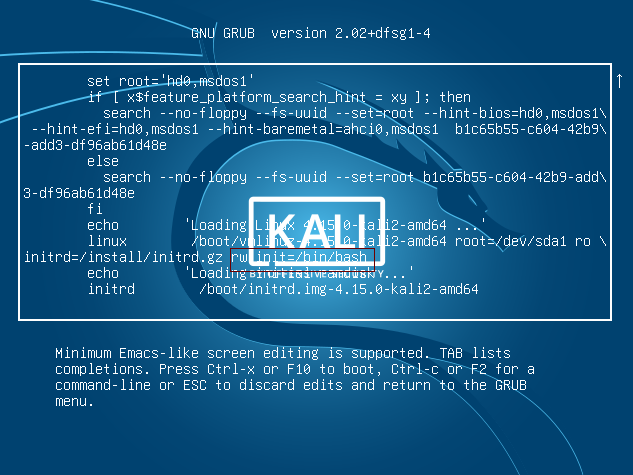
3. Remove the “quiet“ part and add “rw init=/bin/bash” to its place and press “Ctrl+x“
Voila! now you got a root shell to play around with and the possibilities are endless
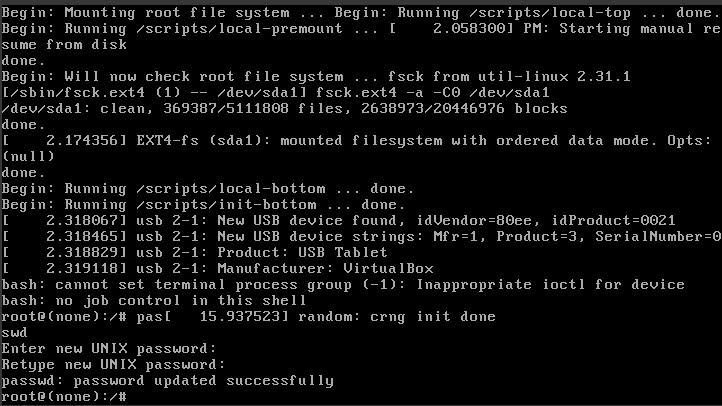
This feature exists on the Linux for the recovery purpose of changing the root password if admin or fixing messed up initialization file, so it is the forgot password? option on Linux OS.
Now its time to get bit technical, what is GRUB and what are we editing here?
when a computer boots up a collection of processes happen throughout the memory.
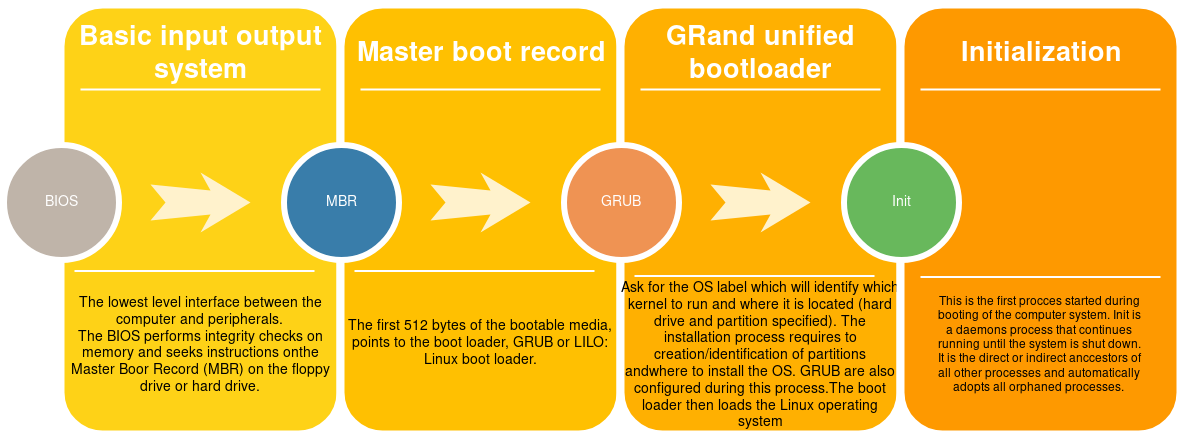
with all of these we use the “init” step to pop a root shell in the system, what we do is instead of using the “sysinit” file, we force the grub to use “init” file and it opens a root terminal. (p.s init is getting replaced by the systemd and there will be a post explaining these two)
The option “quiet” is there to hide booting process but in our case we need to see it so we need to delete the word.
“rw” means mounting the file system so you can read from it and write to it that way the user is capable of doing permanent changes to the system.
Do you see this as a security loophole in your system? there will be a separate post explaining how to harden your system covering this and few other security issues.
